Despite the fact that each proxy server supplies customers with an alternating address, there are numerous sorts of proxy web servers, such as:
- Reverse proxy servers: They commonly rest behind a private firewall software network, as well as path customer data to a certain backend server. The server includes an additional layer of abstraction, as well as control to make sure network website traffic flows smoothly between web servers or clients.
Preparing to Buy Shared Proxy, please click on the link.
- High-privacy proxy server: This proxy server does not allow the original IP address to be identified, as well as no one can recognize it as a proxy server.
- Rotating proxy web server: This proxy server appoints a different IP address to every user that links to it. Customers have appointed an address that stands out from the gadget that is linked prior to them.
- Clear proxy server: This proxy server is additionally referred to as an intercepting proxy, inline proxy, or compelled proxy. This proxy server acts as a middleman between an end-user or device as well as the web. It is referred to as “clear” because it does so without modifying inline proxy, responses or inline proxy.
- SSL proxy server: An SSL proxy server gives file encryption between the client as well as the server. The proxy hides its presence from both the client and the web server since the data is secured in both instructions.
- Web proxy server: An internet proxy server functions as a bridge between a client application, such as an internet browser, as well as the actual server. It sends out demands to the actual server on the customer’s behalf, as well as occasionally meets the case. This kind of proxy web server forwards the HTTP demands.
- Suffix proxy web server: This type of proxy web server includes the proxy’s name to the link of the material asked for by the proxy. You can utilize this sort of server to prevent web filters.
- The Proxy server of DNS: Unlike other proxies, these proxy servers approve DNS questions, as well as forwards them to the domain name web server.
- Confidential proxy server: Users can utilize this sort of proxy server to hide their network traffic’s introduction, so they are not recognized. Proxies allow customers to access web services while concealing key information, such as the computer’s IP address.
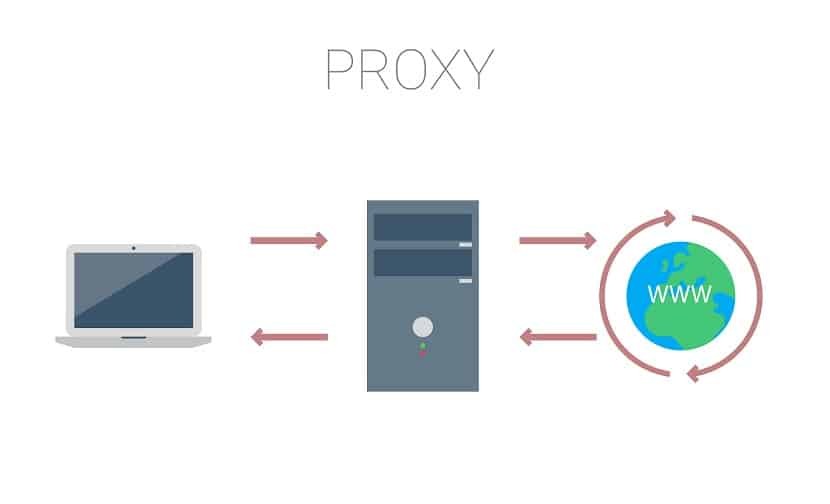
What is the way proxy servers function?
A user typically links to a website by sending a direct request to its internet server by means of their IP address from an internet browser. The internet server then goes back to the user with a response consisting of the internet site data. Whereas, proxy functions as an intermediator for the individual, as well as the web server. Proxy servers utilize various IP addresses on the individual’s part, hiding the individual’s true IP address from internet servers.
You will have a better understanding of how a proxy web server deals with the aid of these steps:
- A person types the URL of a website into their web browser.
- The user’s demand is received by the proxy web server.
- The request is sent to the internet server by the proxy server.
- The internet server goes back to the proxy server with site information.
- The reaction is sent to the individual by the proxy web server.
Option advantages, as well as deliverables
This service is based upon the open-source proxy Squid. The proxy is able to be utilized for every workloads running in the VPC.
Compute Cloud, as well as compute engine.
The solution gives you the following advantages:
- An outgoing proxy that allows links to whitelisted domains that you specify, while offering customizable mistake messages when links are attempted to unauthorized domains.
- Optional domain content filtering system based upon DNS, delivered by exterior solutions. For this choice, you do need to be a consumer of these external services.
- Transparent file encryption handling, because of the extraction of the domain info from the Web server Name Sign (SNI) expansion. Encryption in transit is preserved as well as end-to-end security is kept.
- An auto-scaling group with Network Load Balancers that top several of your existing subnets, and Accessibility Zones, as well as a scale based on CPU loads.
- One Elastic IP address per proxy instance for net interaction. In some cases, the internet site that you are communicating with needs to recognize your IP address, therefore, they are able to approve traffic from you. Providing the proxy’s elastic IP addresses lets you understand what IP your web links will originate from.
- Proxy gain access to logs supplied to Cloud Logs.
- Proxy metrics are offered in Cloud Metrics.
- Automated option implementation using compute engine.
If you want to Buy Europe Proxy from a dependable company, please visit the link.